spring framework linkedin assessment answers
1. A _____ is a key-value map of data used to render the page, and the _____ is a template of the page that is filled with data.
- view; model
- model; view
- hashmap; servlet
- request; view
2. What is the security filter chain?
- It’s a series of user-completed activities-such as password authorization, token verification, and many others-that require multiple factors of authentication to increase the level of security in the system.
- It’s a security filter chain that consumes multiple factors of authentication-such as password, token verification, biometrics, and IP whitelisting-to successfully log a user into the system.
- It’s a servlet filter chain where each filter has a specific responsibility such as security context, user and password authorization, exception translation, or filter security interception, processed in order.
- It’s a security filter chain that provides authentication with manual intervention such that multiple administrators of the system are able to approve users with auditability and traceability.
3. Which of the Service implementations will be created first?

- A NullPointerException is thrown at runtime.
- Service2
- There is no way to know until runtime.
- Service1
4. How are Spring Data repositories implemented by Spring at runtime?
- Spring automatically generates code for you based on your XML config files that define a SpringMethodAutoGeneration factory that intercepts calls to the instance and creates dynamic methods that compute SQL on the fly.
- The Spring JDK proxy creates a separate runtime process that acts as an intermediary between the database and the Web server, and intercepts calls to the instance and handles requests.
- A JDK proxy instance is created, which backs the repository interface, and a Methodinterceptor intercepts calls to the instance and routes as required.
- Spring automatically generates code for you based on your YAML config that defines a Methodlnterceptor chain that intercepts calls to the instance and computes SQL on the fly.
5. What is the default rollback policy?
- When an instance or subclass of RuntimeException is thrown, this triggers a rollback, while any checked Exception does not.
- When an instance or subclass of Exception is thrown, this triggers a rollback, while any runtime exceptions do not.
- A rollback is triggered during any error that occurs during the transaction.
- Antime an instance or subclass of Throwable is thrown, this triggers a rollback.
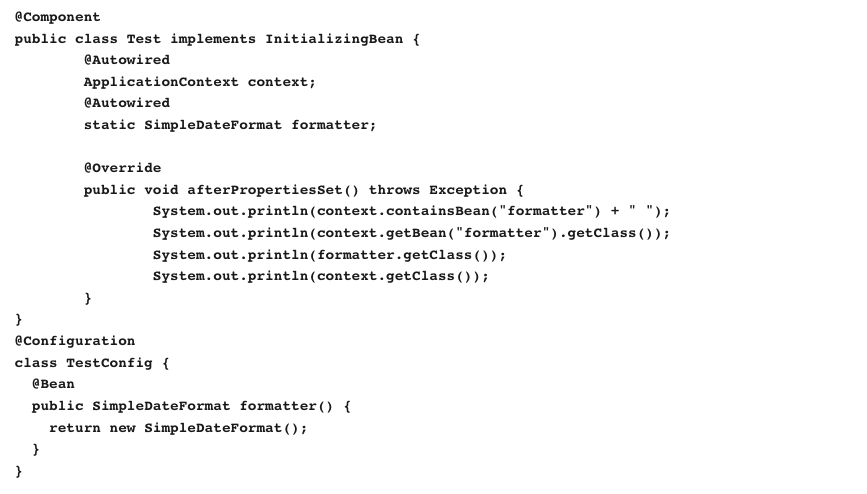
6. Which printin would you remove to stop this code from throwing a null pc Inter exception!
7. What interface is used to represent a permission in Spring Security?
- PermissionMatrix
- SecurityChain
- AccessRule
- GrantedAuthority
8. When configuring an application, which configuration is given precedence b Spring?
- Java System Properties
- application properties located in an application.properties file inside the application.jar
- profile specific application-{profile}.properties files located outside the application.jar
- profile specific application-{profile}.properties files
9. What methods does this Pointcut expression reference?
execution(* com.linkedin.TestService.*(..))
- This Pointcut is not valid.
- all methods of classes in the com.linkedin.TestService package
- all methods defined by the TestService interface
- all methods of classes in the com.linkedin.TestService package annotated with @Service
10. How should passwords be stored?
- Passwords should be hashed using an adaptive one-way function such a bcrypt.
- Passwords should be hashed using the SHA-1 algorithm, then salted to provide defense against rainbow table attacks.
- Passwords can be stored in a BASE64 encoded format if they are stored in a private database.
- Passwords should be salted and hashed using the MD5 algorithm.
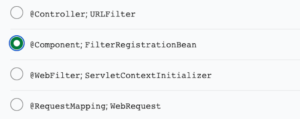
11. To register a custom filter that applies onlv to certain URL patterns, you should remove the _____ annotation from the filter class and register a @Bean of type _____ in Spring @Configuration.
12. What is the difference between constructor injection and setter injection?
- Setter injection creates a new instance if any modification occurs.
- You can’t use constructor injection for partial injection.
- Constructor injection overrides setter injection.
- Constructor injection is more flexible than setter injection.
13. What methods does this Pointcut expression reference?
@target (com.linkedin.annotation.Loggable)
- any method that implements Loggable
- any join point where the executing method has a Loggable annotation
- any method that extends Loggable
- any join point where the target object has a @Loggable annotation
14. What is the result of calling the map controller method using the following Hi IP request:
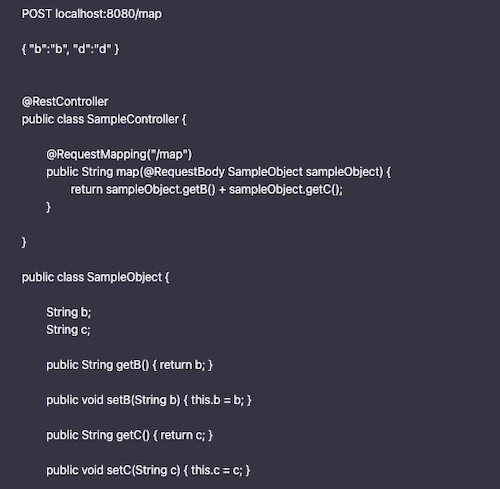
- The text “a” is returned in the response body.
- A MissingPropertyException is thrown at runtime.
- An InvalidRequestBodyException is thrown at runtime.
- The text “bull” is returned in the response body.
15. Which is a valid example of the output from this code (ignoring logging statements)?
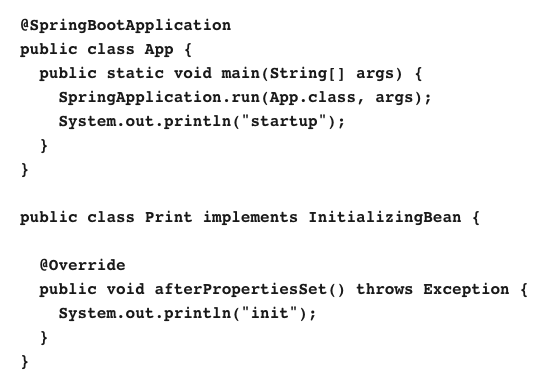
- init
- startup
- Nothing will print.
- startun
init