deploy and maintain assets power bi assets and capstone project coursera week 3 answers
Self-review: Applying sensitivity labels
Introduction
In the exercise Applying sensitivity labels, you helped to secure data in Adventure Works' reports.
As part of this task, you added existing reports to your Power BI workspace and applied and configured data sensitivity labels to secure sensitive information within these reports.
A screenshot of the tasks you completed is included for reference:
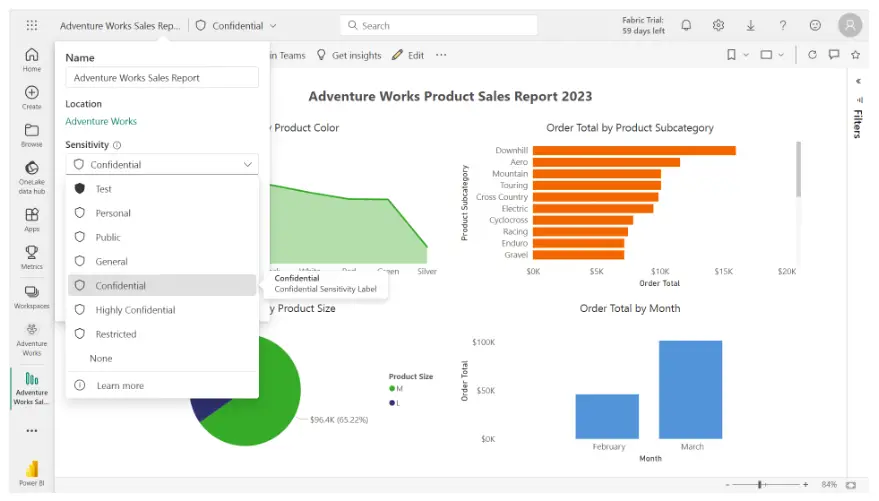
Now it’s time to review your understanding of the tasks you complete by answering the following questions. Don’t forget that you can refer to previous lesson items to recap your process steps.
1. Based on your observation of the Order Total by Product Color visual, which product color has the highest order total?
- Blue

- Red
- Green
2. Based on your observation of the Order Total by Product Category clustered bar chart, which product subcategory has the lowest order total?
- Balance

- Freestyle
- Touring
3. Which label did you apply to ensure the data in the report remains within its shared domain?
- Confidential

- Personal
- General
Knowledge check: Sharing information in Power BI
4. What is the purpose of Row-level security (RLS) in Power BI?
- To ensure data consistency across various reports.
- To display only the data rows that a user’s identity or role permits.
- To encrypt data during transmission for optimal performance.
5. Which security measure in Power BI allows users to work with obscured versions of sensitive data?
- Data encryption
- Data masking
- Roles and permissions
6. What is the primary purpose of the People with Existing Access sharing option in Power BI?
- To nominate individuals by their email addresses.
- To limit viewership to those previously granted permission.

- To avoid sharing with new members of the organization.
7. True or False: The primary reason for ensuring that recipients cannot reshare your report in Power BI is to maintain data integrity and ensure content is viewed only by its intended audience.
- True

- False
8. Which of the following statements are correct descriptions of data sensitivity labels?
- The Restricted label denotes data requiring the utmost secrecy.

- The General label classifies content suitable for a broad audience without specific restrictions.
- The Personal label denotes data linked to specific individuals but not intended for the wider organization.

- The Highly Confidential label safeguards pivotal proprietary information.

Knowledge check: Organizations and permissions
9. Which Power BI dataset permission primarily allows visual representation without altering the source data?
- Write
- Build
- Read
10. What is the primary function of dataset permissions in Power BI?
- To maintain data visibility.
- To ensure selected individuals have specialized access to data.
- To increase the complexity of data access.
- To act as gatekeepers to organizational information.
11. True or False: The primary purpose of the Direct Access tab in Power BI Service is to enable users to grant direct access to specific individuals or groups for a particular dataset.
- True

- False
12. True or False: The primary function of the Links section in Power BI Service is to provide shortcuts to the data source settings and configuration.
- True
- False

13. Which of the following are accurate descriptions of specific Power BI dataset permissions? Select all that apply.
- The Write permission is exclusively about viewing and understanding the data.
- The Reshare permission lets users distribute data to other users or teams.
- The Read permission allows users to modify and delete datasets.
- The Build permission lets users construct visuals and reports without altering the source data.
Knowledge check: Row-level security
14. What does row-level security (RLS) primarily manage in Power BI?
- It manages the interaction and relationship between different data tables.
- It manages the validation of data outputs.
- It manages granular access to data based on predefined roles and rules.
15. How does static row-level security control users' access in their respective data domains? Select all that apply.
- By modifying access levels in response to real-time user activity and role changes.
- By confining users to predetermined and specific segments of data.

- By providing comprehensive insights across different operational domains.
- By relying on DAX expressions to specify boundaries for users.

16. Why is naming a role important when configuring static row-level security in Power BI?
- To facilitate structured management of user access levels.
- To ensure precision in defining visibility boundaries.
- To ensure clarity and avoid potential ambiguities in role management.

17. True or False: Validating configured roles before publishing a report ensures that the data viewed by the user is exactly what they should be seeing.
- True

- False
18. How does dynamic row-level security enhance data accessibility for users with multifaceted roles within a company? Select all that apply.
- By confining users to specific data segments for operational clarity and focus.
- By allowing tailored access to data segments per user permissions.

- By utilizing dynamic filters like USERPRINCIPALNAME() to control data access based on the user’s identity.
- By offering temporary access permissions that expire after a predetermined period.
Self-review: Configuring a data alert
Introduction
In the exercise Configuring a data alert, you identified key report metrics and configured an alert to inform you of the status of these metrics.
As part of this task, you opened and published a report in Power BI, navigated and observed your report data, and managed and configured KPIs and alerts.
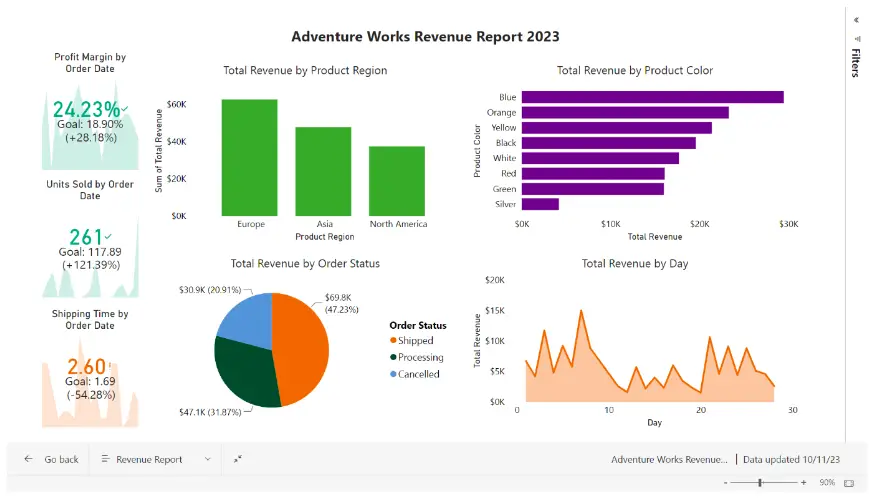
A screenshot of the workspace is included for reference:
Now it’s time to review your understanding of the tasks you complete by answering the following questions. Don’t forget that you can refer to previous lesson items to recap your process steps.
19. True or False: You configured the frequency of the Profit Margin alert to Every 24 hours to monitor the KPI, as this is the optimal regular interval at which you should monitor pivotal metrics related to Adventure Works' financial health.
- True
- False

20. What threshold percentage did you configure for the profit margin for triggering the alert?
- 10%
- 20%
- 15%
21. What was the primary purpose of pinning the ProfitMargin KPI to a dashboard in the exercise?
- To ensure that the KPI is easily accessible for monitoring.

- To emphasize the importance of the KPI in Adventure Works’ financial health.

- To allow team members to share KPIs with external stakeholders.
- To facilitate a streamlined workflow in Power BI.
Knowledge check: Subscriptions and alerts
22. What are the benefits of setting up subscriptions in Power BI? Select all that apply.
- Subscriptions ensure real-time collaboration on reports, allowing teams to make changes simultaneously.
- Subscriptions establish a shared understanding within teams when making decisions if all members are subscribed to the same reports.
- Subscriptions provide instant updates, ensuring subscribers always have the most current data.
- Subscriptions boost efficiency and productivity by reducing the time data analysts spend manually retrieving reports.
23. True or False: When you set up a subscription in Power BI, the primary aim is to create new reports and dashboards based on live data feeds.
- True
- False
24. How do data alerts enhance collaboration within teams?
- By integrating with other collaboration tools in Power BI.
- By sending notifications about weekly insights to team members.
- By offering shared dashboards for team review.
- By notifying relevant parties about critical data-driven insights.
25. True or False: Data alerts in Power BI send notifications when metrics go above or below a predefined threshold.
- True
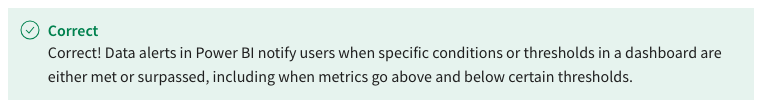
- False
26. Which type of visuals in Power BI can you set alerts on?
- Pie charts and bar graphs.
- Histograms and tree maps.
- Gauges, KPIs, and cards.
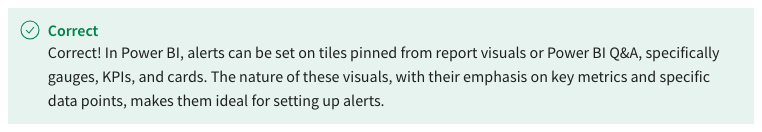
- Line graphs and scatter plots.
Module quiz: Security and monitoring
27. True or False: Sharing a report using Power BI's People in your organization option restricts access only to those you've previously granted access.
- True
- False
28. Which of the following statements about Power BI's sharing permissions are true? Select all that apply.
- Reshare permissions allow the initial recipient of a report to share it further with others.

- Reshare permissions can lead to the original context of the shared data being diluted with subsequent shares.

- Build permissions allow individuals to use shared data to create new reports.
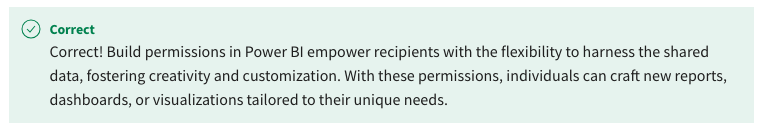
- Build permissions grant recipients administrative rights over the original report.
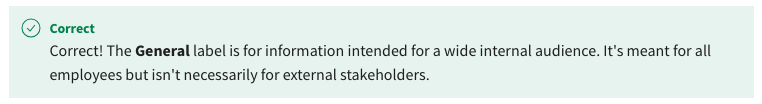
29. True or False: The General sensitivity label in Power BI is primarily for data targeted at external stakeholders containing specific sensitivities.
- True
- False
30. A new team member has been assigned the Write permission for a report. They ask you what this new responsibility entails. How would you explain the permission?
- They can modify the actual datasets in Power BI.
- They’re limited to resharing existing datasets and reports without making any changes.
- They can only view and understand datasets without modifying them.
31. True or False: Power BI uses dynamic row-level security (RLS) to adjust and change the data a user can access based on their current role or focus.
- True

- False
32. You’re configuring static row-level security in Power BI for Adventure Works. What actions are most critical to ensure that only designated personnel can access specific data? Select all that apply.
- Renaming the role to a more descriptive name to avoid ambiguities.

- Publishing the report before testing the DAX expression.
- Sharing the configurations with external stakeholders for approval.
- Testing the configuration using View as Roles.

33. What information does the USERPRINCIPALNAME( ) function retrieve?
- The user’s email address.

- The user’s department.
- The user’s job title.
34. What is the main purpose of the subscription feature in Power BI?
- To set up automated delivery for reports and dashboards.

- To automate the creation of new reports from scratch.
- To allow users to share reports on internal organization platforms.
35. At Adventure Works, the marketing team wants to monitor their latest campaign using data alerts through a Power BI dashboard. On what dashboard visuals can they set up real-time alerts?
- Alerts can be set on Power BI Q&A visuals.
- Alerts can be set on pinned tiles, gauges, KPIs, and cards.

- Alerts can be set on any visual in a Power BI report.
36. Which statement best describes the primary distinction between static and dynamic row-level security (RLS)?
- Static RLS requires periodic manual updates for role changes, while Dynamic RLS remains static unless data changes significantly.
- Static RLS provides fixed data access based on pre-defined roles, whereas Dynamic RLS adapts access based on user attributes or roles.

- Static RLS uses user attributes, such as USERNAME(), while Dynamic RLS uses DAX filters to assign access.
37. You recently wrote a report for Adventure Works and must share this report with specific organization members. What methods can you use to share your report using Power BI's link-sharing feature? Select all that apply.
- Use the Copy link option to generate a unique URL.
- Directly email the report as an attachment to desired recipients.
- Share it with People in your organization.

- Share it with People with existing access.
38. You’ve created a report for Adventure Works and wish to share it with the marketing and sales departments. However, you're wary about accidentally sharing the report with other departments. How can you use Reshare permissions to manage who you share the report with?
- It allows you to share the received report with others.

- It restricts you from viewing certain parts of the report.
- It permits you to update the content of the original report automatically.
39. You're working on a Power BI project requiring data to be classified based on confidentiality using sensitivity labels. Which labels can you apply in Power BI for classifying data? Select all that apply.
- General

- Public

- Personal

- Internal
40. True or False: An individual equipped with the Build permission in Power BI datasets is strictly limited to reading and resharing datasets, unable to make direct modifications.
- True
- False

41. How would you best describe the primary purpose of RLS in Power BI?
- It controls access to the data residing in the columns of a table.
- It creates relationships between tables and models in Power BI based on user roles.
- It controls access to the data residing in the rows of a table based on user roles.
42. Which statements best describe the advantages of Power BI data alerts? Select all that apply.
- They promote proactive problem-solving.
- They are customizable and personalized to the user’s needs.

- They help to streamline the IT infrastructure.
- They save time and increase efficiency.
43. You are working on a Power BI report containing strategies for the upcoming quarter, including campaigns, promotions, and partnerships. Which data sensitivity label is most appropriate for this kind of report?
- General
- Restricted
- Confidential

44. Which of the following statements correctly describes the permissions available in Power BI datasets? Select all that apply.
- The Owner permission allows users to create visuals and reports without modifying the source data.
- The Write permission enables users to modify the actual datasets in Power BI.
- The Reshare permission lets you distribute specific datasets or reports to other users or groups.
- The Read permission allows team members to access and view datasets without changing the original content.

45. Which of the following actions should you take when implementing dynamic row-level security? Select all that apply.
- Use the USERPRINCIPALNAME( ) function to correlate data rows with user identities.

- Assign specific data access roles to different users.
- Use DAX formulas to create dynamic data filters.

- Merge data tables to reduce the number of tables to maximize security.
46. In which scenario would Adventure Works most likely benefit from dynamic RLS in Power BI?
- Providing consistent access to sales data for managers.
- Permitting access to data for users switching between sales and manufacturing roles.
- Granting access to marketing data based on an employee’s assigned campaigns.
